-
Systrace for Mac OS X
Systrace enforces system call policies for applications by constraining the application's access to the system. The policy is generated interactively. Operations not covered by the policy raise an alarm and allow an user to refine the currently configured policy. Systrace for Mac OS X supports the same features as the *BSD versions. However, due to the Mac OS X design, Systrace currently works only for native Unix applications. More work is required for full support of Mac OS X. Systrace is still in Beta testing and I would appreciate feedback about its stability.
- Systrace Mac OS X package
- Requires Mac OS X 10.2. - 2002-12-04
- This package installs a new kernel that supports the /dev/systrace device and the Systrace application. If the boot path to the new kernel has been lost, it can be recovered by reinstalling the Systrace package.
- You can find more up-to-date builds of Systrace at http://www.opendarwin.org/~fkr/.
- The sources for Systrace itself are available on the main page.
- Darwin Kernel diff - apply in src/xnu. - 2002-12-03
-
Cocoa-Systrace - graphical
Mac OS X frontend to Systrace. 2002-12-03
- Not yet feature complete, but provides basic functionality.
For more information, please check the main Systrace page. Systrace is part of my effort to improve host security. My earlier work on Privilege Separation has already been integrated into Mac OS X.
Features
- Confines untrusted binary applications.
- Interactive Policy Generation with Graphical User Interface.
- Supports different emulations:
- GNU/Linux, BSDI, etc..
- System Call Argument Rewriting.
- Non-interactive Policy Enforcement.
- Remote Monitoring and Intrusion Detection.
- Privilege Elevation: Add-on capabilities.
Screenshots
Systrace connected to a Cocoa graphical frontend. iTunes running under Systrace. 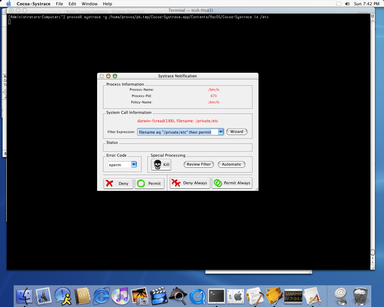
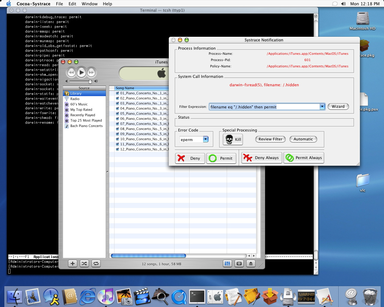
Sample Policies
- iTunes - Policy for the iTunes music player that allows playing of music from a User's music folder.
As I returned the loaned Powermac G4, futher improvements have to wait until I get access to a machine again. If you know of someone who could donate a machine for this purpose, please let me know.Acknowledgements
Thanks to Jean-Pierre Mouilleseaux for providing temporary access to a Powermac G4 machine so that I could port Systrace. - Systrace Mac OS X package
- Requires Mac OS X 10.2. - 2002-12-04